Wutawhacks Columns Trigger Alarms as Cybersecurity Experts Warn Users
The internet does not usually announce danger with sirens. It whispers first. Over the past few days, those whispers have grown louder around one phrase quietly climbing search trends in the United States: wutawhacks columns. What started as niche chatter among cybersecurity watchers has now spilled into mainstream concern, triggering anxiety about privacy, data exposure, and how prepared everyday users really are for the next digital shock. This story is not just about hackers. It is about awareness, timing, and what happens when obscure online spaces suddenly matter.
Table of Contents
ToggleWhat Are Wutawhacks Columns and Why They’re Trending Now
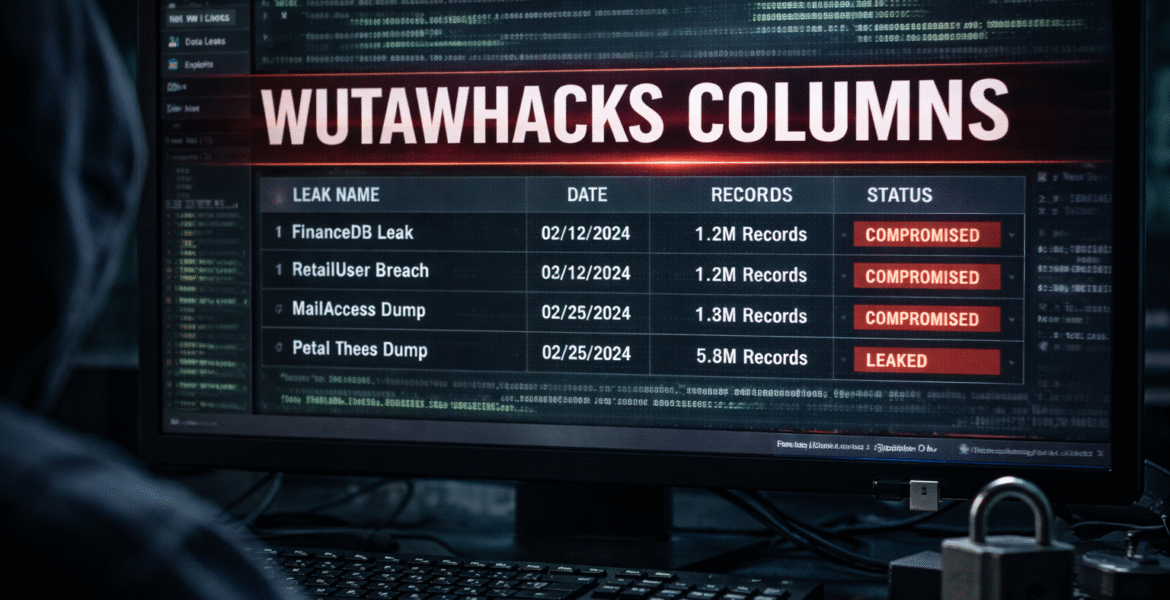
Wutawhacks columns refer to structured data listings and discussion threads that appear within the Wutawhacks ecosystem, a lesser-known but fast-growing hackers forum often mentioned alongside underground breach-sharing communities. These columns typically organize leaked data, vulnerabilities, or breach references in a readable, categorized format. While such structures are common in technical spaces, their sudden visibility has raised red flags across cybersecurity circles in the United States.
The trend surged after multiple security researchers noted that wutawhacks columns were being referenced in external forums, breach monitoring tools, and even social media posts. The concern was not just their existence, but their accessibility. When organized breach-related data becomes easy to scan, it lowers the barrier for misuse. Experts warn that visibility often precedes exploitation, especially when sensitive information is involved.
How Cybersecurity Researchers Discovered the Wutawhacks Columns
The discovery of wutawhacks columns did not come from a single dramatic leak. Instead, it unfolded gradually through routine monitoring by independent cybersecurity analysts and ethical hacking groups. Many researchers track underground forums to anticipate emerging threats. In late reports, analysts noticed repeated references to “columns” within Wutawhacks discussions, suggesting a systematic approach to data sharing.
What made this discovery notable was the consistency. The columns appeared to follow similar formatting patterns, listing breach names, timestamps, and sometimes sample data indicators. While not all entries contained sensitive information, the structure itself signaled organization. In cybersecurity, organization often means scale. That realization prompted deeper investigation and quickly pushed the topic into trending territory.
Why Wutawhacks Columns Raise Serious Privacy Concerns
At the heart of the alarm surrounding wutawhacks columns is privacy. Organized data, even without full exposure, can act as a roadmap for malicious actors. Cybersecurity experts emphasize that columns can function as indexes, pointing users toward where sensitive data might be found or purchased. For everyday Americans, this raises the risk of identity theft, phishing, and financial fraud.
Privacy advocates argue that the danger lies in aggregation. A single leaked email may seem harmless, but columns that connect emails, passwords, and breach histories paint a much clearer picture of an individual’s digital life. This is why wutawhacks columns are being discussed alongside data breach risks and dark web monitoring, even if the platform itself remains relatively obscure.
The Role of Hacker Forums in Shaping Digital Threats
Hacker forums have long played a complex role in the cybersecurity landscape. Not all participants are criminals; many are researchers, hobbyists, or ethical hackers. However, platforms like Wutawhacks blur those lines. Wutawhacks columns, in particular, demonstrate how forums evolve from discussion spaces into functional data hubs.
In the United States, law enforcement agencies and cybersecurity firms monitor such forums because they often signal emerging attack patterns. Historically, similar forums have preceded major breaches by months. The structured nature of wutawhacks columns suggests maturity, which experts say often correlates with increased activity and higher stakes. That is why their appearance is being taken seriously, not dismissed as internet noise.
What the Data Tells Us About Rising Cyber Threats
Statistics help explain why this story resonates now. According to recent industry reports, data breaches in the United States increased by more than 70 percent over the past year. Millions of Americans have had personal data exposed, often without immediate notification. In that climate, any new system for organizing breach information draws attention fast.
Wutawhacks columns fit into a broader trend of cybercriminal efficiency. Automation, categorization, and searchable formats reduce effort and increase reach. Cybersecurity analysts note that when threat actors spend less time organizing data, they spend more time exploiting it. That shift alone makes the emergence of these columns a noteworthy development in the ongoing cybersecurity battle.
How Companies and Users Are Reacting to the Trend
Corporate security teams were among the first to react. Several U.S.-based companies quietly reviewed their breach monitoring protocols after wutawhacks columns began circulating in professional forums. While no major corporation has publicly confirmed a direct link, internal advisories reportedly mentioned the platform as “one to watch.”
Individual users, meanwhile, are reacting with confusion and concern. Search spikes show Americans asking whether their data appears in wutawhacks columns and what steps they should take. Cybersecurity educators stress that panic is unnecessary, but awareness is critical. Password hygiene, two-factor authentication, and credit monitoring remain the most effective defenses for now.
Ethical Hacking and the Gray Area of Data Sharing
One of the most debated aspects of wutawhacks columns is intent. Some argue that structured data sharing can serve defensive purposes, helping researchers identify patterns and warn the public. Ethical hacking communities often rely on shared knowledge to strengthen systems. However, critics counter that open accessibility undermines any ethical justification.
This gray area complicates the narrative. Not every mention of wutawhacks columns implies criminal activity, but the potential for abuse is undeniable. In the United States, where digital privacy laws remain fragmented, such ambiguity leaves users vulnerable. The conversation now extends beyond one platform to broader questions about responsibility in online security spaces.
What Experts Predict Will Happen Next
Looking ahead, experts predict increased scrutiny of Wutawhacks and similar platforms. Cybersecurity firms are likely to expand monitoring, while law enforcement agencies may quietly gather intelligence. Historically, when forums gain mainstream attention, they either adapt, fragment, or disappear. Wutawhacks columns could evolve, become restricted, or move to more hidden networks.
For users, the prediction is less dramatic but equally important. Awareness will rise, leading to more proactive security behavior. Industry analysts believe that stories like this push cybersecurity from a niche concern into everyday conversation. If history is any guide, today’s trending keyword often becomes tomorrow’s cautionary lesson.
Why This Moment Matters for Digital Safety in America
The sudden spotlight on wutawhacks columns is about more than one forum. It reflects a broader shift in how digital threats emerge and spread. In an era where data is currency, organization equals power. When obscure systems gain structure, they gain influence. That reality makes this trend relevant to every American who lives, works, and shops online.
Digital safety is no longer just a technical issue. It is a social one. The attention around wutawhacks columns shows how quickly hidden corners of the internet can impact mainstream life. Staying informed is no longer optional; it is essential.
If you found this report eye-opening, stay informed by following trusted cybersecurity news sources, review your digital security settings today, and share this article to help others understand why online awareness matters now more than ever.